Usually, providers don’t spend much time on offering a simple and detailed way to update the self-signed certificate they provide with their appliances.
I was disapointed to see that Nessus, which will basically complains all the time about the wrong certificate mismatch it will discover on your networkd, doesn’t provide an easy way to replace its own ugly certificate.
The funny part is, you will see it at least once within the scan result, because of this wrong certificate, what a shame isn’t it?!
Generate a custom cert and a key, using Base 64 encoding
As the title says, you can use whatever way you want to generate a new .cert and a new .key file, that’s mandatory.
The following is related to my own way to do it, I’m writing that here for the records, I suggest you to skip to the next heading.
- Use OPNSense Certificate tool to generate a CSR
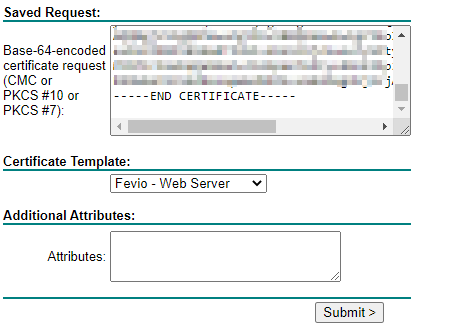
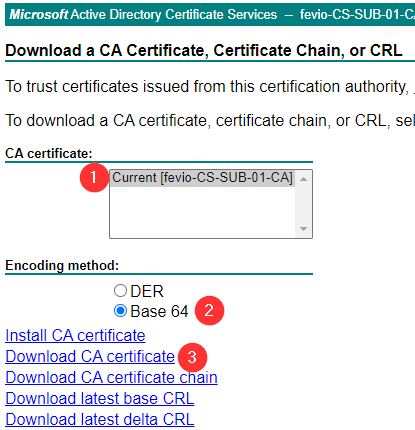
- Submit the CSR to the AD CS certsrv tool and get your certificate, base 64 encoded
- Download from OPNSense the associated .key
Install the certificate and the key on your Nessus server
First, stop the Nessus daemon, on Ubuntu 20.04:
/etc/init.d/nessusd stopEdit the curent certificate with the following command:
vim /opt/nessus/com/nessus/CA/servercert.pemRemove its content, and replace it with the content of your new certificate.
Then, edit the former key file, with the command below:
vim /opt/nessus/var/nessus/CA/serverkey.pemDo the same thing, replace the content with the one contained on your key file.
Eventually, start the Nessus server to get your server back online:
/etc/init.d/nessusd startThat was not complex, but I would have appreciate:
- A way to generate the CSR from the Nessus GUI
- An obviously, a way to import the certificate as well