version: "2"
services:
postgresql:
image: 'postgres:latest'
container_name: guacamole_db
ports:
- 5432:5432
environment:
POSTGRES_USER: guacamole_postgres # The PostgreSQL user (useful to connect to the database)
POSTGRES_PASSWORD: YourOwnPassword # The PostgreSQL password (useful to connect to the database)
POSTGRES_DB: guacamole # The PostgreSQL default database (automatically created at first launch)
guacd:
image: "guacamole/guacd"
container_name: guacd
hostname: guacd
restart: always
volumes:
- "/data/shared/guacamole/guacd/data:/data"
- "/data/shared/guacamole/guacd/conf:/conf:ro"
expose:
- "4822"
ports:
- "4822:4822"
network_mode: bridge
guacamole:
image: "guacamole/guacamole"
container_name: guacamole
hostname: guacamole
restart: always
volumes:
- "/data/shared/guacamole/guacamole/guac-home:/data"
- "/data/shared/guacamole/guacamole/conf:/conf:ro"
expose:
- "8080"
ports:
- "8088:8080"
network_mode: bridge
environment:
- "GUACD_HOSTNAME=localhost"
- "GUACD_PORT=4822"
- "POSTGRES_PORT=5432"
- "POSTGRES_DATABASE=guacamole"
- "GUACAMOLE_HOME=/data"
- "POSTGRES_USER=guacamole_postgres"
- "POSTGRES_PASSWORD=YourOwnPassword"
- "POSTGRES_HOSTNAME=localhost"Go ahead and spin it
docker-compose up -dNow we need to init the database
docker run --rm guacamole/guacamole /opt/guacamole/bin/initdb.sh --postgresql > initdb.sql
docker container cp initdb.sql guacamole_db:/
docker container exec -it guacamole_db psql --dbname=guacamole --username guacamole_postgres -f /initdb.sqlBelow the old way version (not working properly regarding the guacacd part)
Here a really quick draft to setup a Guacamole RDP server using a docker container and PostgreSQL
# Get the latest image
docker pull guacamole/guacamole
# Create volumes to persist data
docker volume create guacamole-vol-app
docker volume create guacamole-vol-db
# Create the dedicated network
docker network create --driver bridge guacamole-netConfigure the database:
# Spin up the container
docker run --detach --restart unless-stopped -v guacamole-vol-db:/var/lib/postgresql/data --network guacamole-net --name gcm-db-01 -e POSTGRES_PASSWORD=aRandomPasswd postgres
# Connect to the container
docker exec -it gcm-db-01 bash
# Then to PostgreSQL
psql -U postgres
# Create the DB
CREATE DATABASE guacamole WITH ENCODING 'UTF8' LC_COLLATE='en_US.UTF-8' LC_CTYPE='en_US.UTF-8' TEMPLATE=template0;
create user guacamole_postgres with password 'randomPassword';
GRANT ALL PRIVILEGES ON DATABASE guacamole to guacamole_postgres;
# Quit
\q
# Quit the container
Ctrl+p then q
# The following command will generate a file to be used for DB initialization
docker run --rm guacamole/guacamole /opt/guacamole/bin/initdb.sh --postgres > initdb.sql
# Copy the file to the container
docker container cp initdb.sql gcm-db-01:/
# Execute the file
docker container exec -it gcm-db-01 psql --dbname=guacamole --username postgres -f /initdb.sqlConfigure your container:
# Pull GuacaCD
docker pull guacamole/guacd
# Generate the GuacaCD proxy
docker run --name gcm-cd-01 --network guacamole-net -d guacamole/guacd
docker run --name gcm-app-01 --network guacamole-net \
-e POSTGRES_HOSTNAME=gcm-db-01 \
-e POSTGRES_DATABASE=guacamole \
-e POSTGRES_USER=guacamole_user \
-e GUACD_HOSTNAME=gcm-cd-01 \
-e TOTP_ENABLED=true \
-e POSTGRES_PASSWORD=aRandomPasswd \
-d -p 8003:8080 guacamole/guacamoleTOTP_ENABLED=true enable a WhateverAuthenticator app to add another level of security.

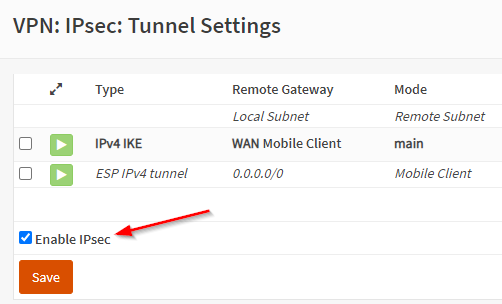
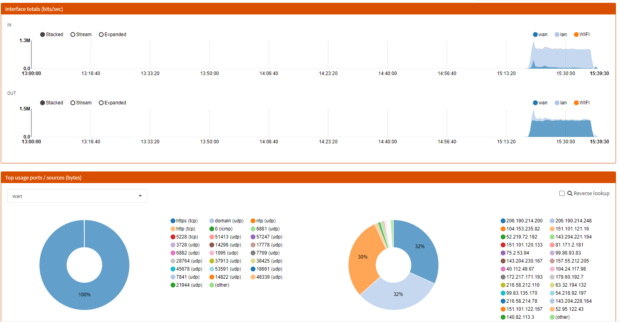

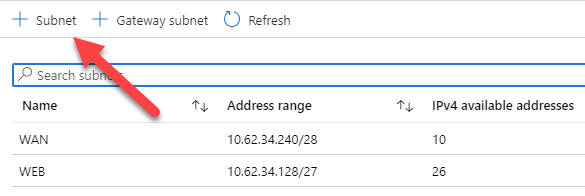
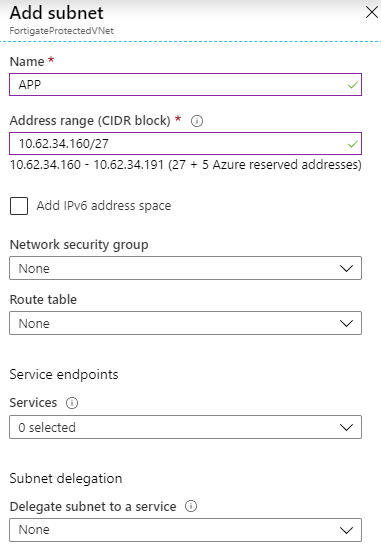
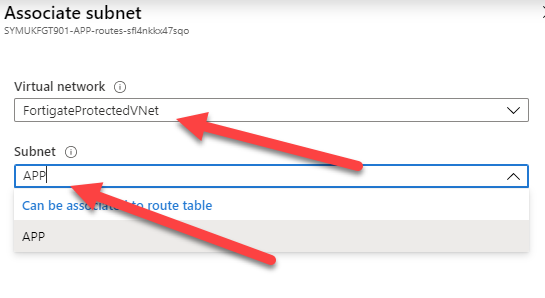
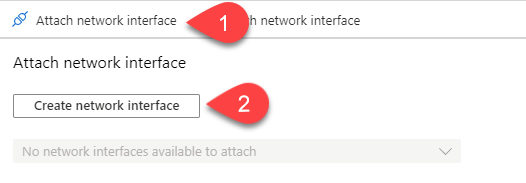
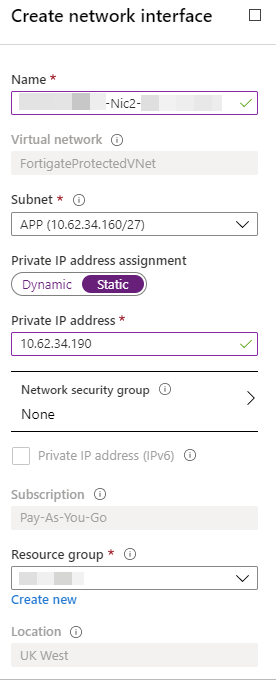
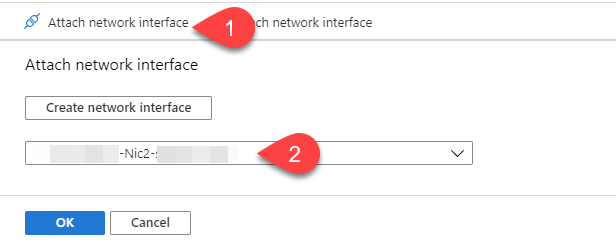
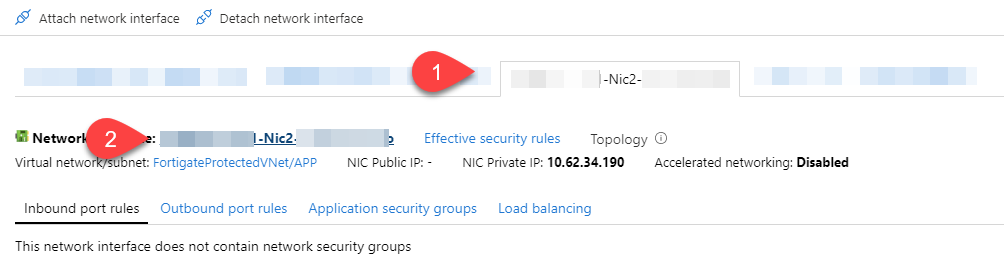
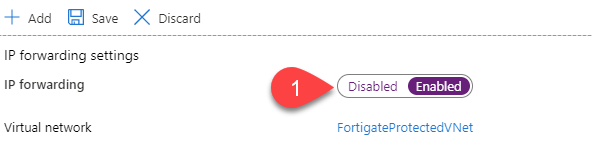
 Before moving further, at this time, there is no way to configure your Azure network to push another gateway that the Azure default to your machine, you can create route for the next-hop, but those routes can’t override the default gateway. Long story short, you will have to manually configure the default gateway of your servers to make them use your Fortigate as their next-hop.
Before moving further, at this time, there is no way to configure your Azure network to push another gateway that the Azure default to your machine, you can create route for the next-hop, but those routes can’t override the default gateway. Long story short, you will have to manually configure the default gateway of your servers to make them use your Fortigate as their next-hop.